Smart contracts, blockchain and decentralized computing

[gpt3]rewrite
Decentralized networks are becoming commonplace in today’s tech landscape, as companies seek to write custom applications that solve business problems. These are increasingly based on smart contracts — structured programming logic that runs on a blockchain that runs on a decentralized network. Smart contracts and blockchain apply to a wide range of commercial sectors, including agriculture, finance, real estate and industrial production.
This article covers the basic principle of decentralization: what it is, how it works, and how it is used to manage applications such as blockchain-based smart contracts.
Centralization vs decentralization
Let’s start by understanding the difference between centralization and decentralization.
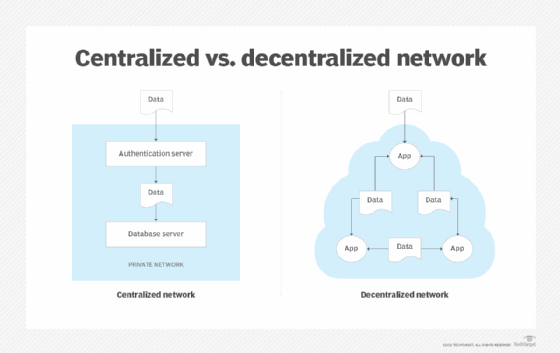
How a centralized network works
In a centralized network, a central authority determines which data can be stored on the network and grants varying levels of access to this data.
A simple way to conceptualize a centralized network is to imagine a bank that keeps all its applications and data on a private network. Customers opening accounts at a bank provide a username and password, along with personal information. The bank stores all this in a database located on its private network.
The bank implements many restrictions to access the applications and data on its network. Customers provide a username and password to access and work with applications and data, but they only have access to what the bank has given permission for. They cannot see the data of other customers, nor can they access applications or data reserved for bank personnel, for example for processing loans. No bank allows anyone to audit its books; the auditor must be authorized by a person in charge. However, banks may allow the public to access and view certain data, such as information relating to advertising or for support purposes.
Everything is subject to the bank’s central authority, which determines which data can be stored on the network and gives a certain degree of trust and permission to a given user.
How a decentralized network works
Decentralized computing is an architectural style in which there is no central point of authority to control access to data or logic residing in a network. Instead, authority is determined according to algorithms shared by all computers, or nodeswhich is part of the network.
Decentralized networks work on a peer-to-peer basis. Each computer or node on the network has an exact copy of all the network’s data and applications, and if one receives additional data, it forwards this data to the other nodes on the network.
Imagine a network of computers, each of which has only one particular text editor and a collection of the same text documents. Anyone can use any computer on that network and have the same computing experience, meaning they can read any text document in the collection using the installed text editor.
Let’s say someone using one of these computers creates a new document with the installed text editor and saves it to the local disk. The computer then sends the saved document to all the other computers on the network. Furthermore, when a computer on the network receives a new document, it does two things:
- It checks the local hard drive to see if it already has the document, and if so, ignores the supposed new document.
- It sends the new document to all the other computers on the network.
The result is that all computers on the network are in the same state in terms of applications (text editing) and data (collection of documents), unless and until a new document is introduced into the network.
This is essentially how decentralization works. There is no single central authority that determines which data can be stored on the network and which gives access to applications and data on the network. Instead, all the computers on the network have the same data and applications, and their data and application configurations are identical. Anyone can audit the data on the network.
How decentralization applies to blockchain and smart contracts
Decentralization is the principle that makes blockchain and smart contracts work.
As the name suggests, blockchain stores data in immutable blocks that are linked together in sequence. Each additional block in the chain is represented by a hash that describes the contents of the current block under construction, as well as all the contents of each previous block in the chain. This process ensures that data is correct throughout the chain, with each additional block, and preserves the blockchain’s data integrity.
Blockchains treat each new block the same way, much like the text editor/document scenario described above. New blocks are sent to all other computers on the network, who add the new block to their instance of the blockchain. Every computer on the blockchain network has an identical copy of the blockchain data. Thus, the blockchain network is decentralized. If one computer on the network stops working, it doesn’t matter because other computers on the network have the same data and the same data algorithms.
Decentralization and cryptocurrency
Industrial decentralized networks first appeared with cryptocurrencies. Cryptocurrencies are not operated by any single entity; no central bank creates the money. Probably the most famous cryptocurrency around is Bitcoin, created in 2009, which uses blockchain technology as its data storage mechanism.
Tools like Blockchain Explorer allow you to see the movement of Bitcoin from one account to another through the decentralized network, as well as see the transaction behavior on other cryptocurrency networks. The private banking industry has no equivalent tool to provide such visibility – and will never publish one either.
There are many more details in the decentralization architecture that synchronize the blockchain among all the computers on the network and also make it difficult for malicious actors to counterfeit cryptocurrency or steal cryptocurrency from user accounts. What is important to understand about Bitcoin and other cryptocurrencies is that they operate on decentralized networks. No computer or agent is responsible for the blockchain.
Despite recent turmoil – the failure of the FTX exchange and the falling value of popular cryptocurrencies such as Bitcoin and Ether, for example – conservative estimates indicate that the overall cryptocurrency market is around 1 trillion dollars. Even if half the money disappeared tomorrow, what remains would still exceed Austria’s GDP. Cryptocurrency is here to stay and it has proven the value of decentralization.
How Do Decentralized Networks Address Security?
An important consideration with decentralized networks is security, especially around user identity. Centralized control means a single security authority, but decentralization throws that model out the window. Businesses that rely on smart contracts must trust the legitimacy of the blockchain. Those who support cryptocurrencies do not want to be put in a position where they support criminal activities such as money laundering.
A user is typically represented in a cryptocurrency network by a account identifier — ie, a unique value expressed as an alphanumeric string.
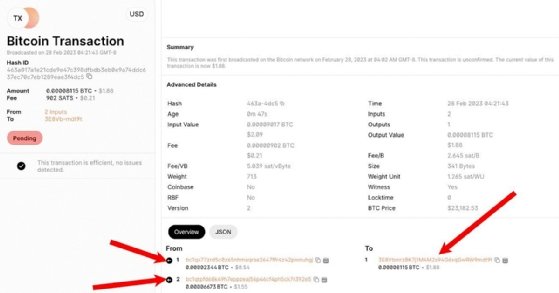
An account identifier is tied to a digital component called a wallet. Information about the holder of the wallet, such as name, email and other access information, is private to the wallet. All user information in a wallet is stored on a local machine, not in a private network or somewhere in the cloud. A wallet may be tied to a variety of cryptocurrency networks, but this information is private to the user, as is their identity information.
However, there are situations that require more information to be known about a user beyond the account identifier. The decentralized identity model, also known as self-sovereign identity, is sponsored by the World Wide Web Consortium to address the sharing of personal information in a decentralized manner. Under decentralized identity, users own their identity information and share parts or all of it. No central authority provides access to a user’s information, such as how Google’s login provides user verification via OAuth. Instead, users store their identity information in a decentralized, encrypted manner, and when an identity needs to be verified, the user decides what information to share with a particular network.
Programs such as the decentralized identity model are still under development. The important thing to understand is that decentralization and private identity management are essential to running decentralized networks.
Put everything together
When the internet first appeared on desktop computers, many saw it as just a better way to send email and a new way to look at cat pictures. Today, the internet is at the center of all social and commercial activity.
The potential of decentralized network and blockchain technology – as represented in various initiatives considered Web3 – has the same potential. As more companies adopt smart contracts and support cryptocurrencies in their daily activities, they will explore new new ways to use these technologies.
[gpt3]
























