Halborn Finds Zero-Day Hacks Affecting Over 280 Crypto Networks

Vulnerabilities in crypto networks remain rife in 2023 after a disastrous 2022. In the latest example, a security research team revealed huge risks in Dogecoin, Litecoin and Zcash, with developers warning of further risks.
Cryptocurrencies use an open source code base designed to allow anyone to inspect, modify and distribute the software’s source code. This transparency promotes transparency, accountability and innovation, and enables the crypto community to continuously develop and improve blockchain technology.
However, it also means that the code is vulnerable to exploitation by malicious actors who can identify and exploit its weaknesses.
Different Ways bad actors can penetrate the network
Here are some ways open source codebase can have vulnerabilities that can affect the security of the blockchain.
- Code errors: Even the most experienced developers can make code errors that can leave the code open to exploitation. For example, a developer could create a vulnerability by failing to perform proper input validation, allowing an attacker to inject malicious code into the system. Likewise, an error in memory allocation or data handling can cause data corruption or leaks.
- Lack of code review: Open source codebases rely on peer review to identify and fix problems in the code. However, if the codebase lacks a rigorous review process, it can lead to security holes that attackers can exploit. In addition, inexperienced developers who make changes without understanding the implications of their modifications can introduce new vulnerabilities.
- Forked code: Forking is a process where developers modify an existing codebase to create a new project. Although forking is expected in the open source community, it can introduce vulnerabilities if developers fail to incorporate security patches or make erroneous changes. If a forked project becomes popular, attackers can target it because of its potential vulnerabilities.
- Software Dependencies: Many open source projects function correctly by using third-party libraries and frameworks. While these dependencies can save time and effort, they can also introduce vulnerabilities if they contain bugs or are outdated. Attackers can exploit these vulnerabilities to gain access to sensitive data or compromise the integrity of the blockchain.
- Social Engineering: Even if the codebase is technically sound, attackers can still exploit human weaknesses to gain access to the system. For example, they can use phishing attacks to obtain login information or trick developers into introducing malicious code into the system.
Crypto platforms are seeing an increase in illegal activities
In conclusion, the open source of the cryptocurrency codebase provides significant benefits, such as openness and innovation. However, it also introduces potential vulnerabilities that attackers can exploit. Therefore, developers must continuously review and improve the code to ensure its security and maintain the integrity of the blockchain.
Bad actors involved in cryptocurrency hacking rose by $3.80 billion last year. Illegal activities in 2022 were up 15% compared to 2021 figures ($3.30 billion) and up dramatically from the $0.50 billion stolen in 2020.
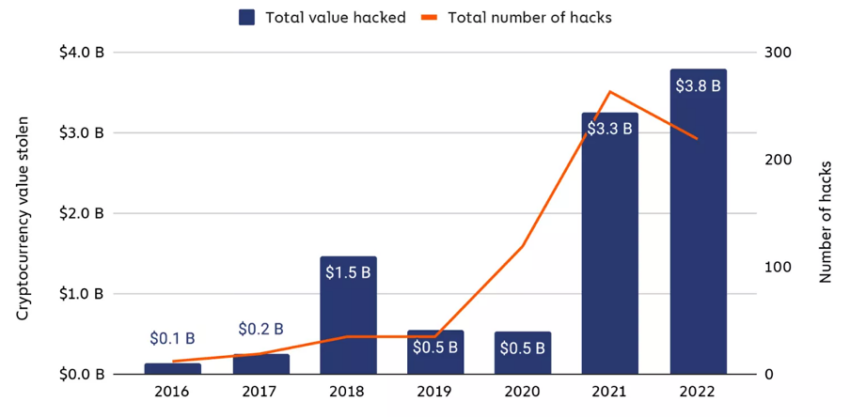
According to a finding by cyber security firm Halborn, 2023 could be even more disastrous. Vulnerabilities were discovered in over 280 major blockchains. These include Dogecoin, Litecoin and Zcash. In total, around $25 billion was put at risk.
Highlighting the main loophole
Halborn researchers evaluated DOGE’s open-source codebase to test for unknown exploits, or “zero-day vulnerabilities,” in its code that could target blockchain miners’ funds.

Researchers identified two critical gaps codenamed Rab13s. The Dogecoin developers later fixed the bugs after being alerted by the security firm.
Serious consequences of malicious events
Identifying loopholes raised more doubts as variants of these zero days were also discovered in similar blockchain networks, including Litecoin and Zcash. Keeping the holes in the back of your mind can lead to serious consequences.
First, regarding the P2P messaging mechanisms, malicious consensus messages can be sent to each node, causing them to shut down and exposing the network to serious risks such as 51% attacks. Furthermore, attackers can run code through the public interface (RPC) as a normal node user. The probability of an exploit is lower since a valid credential is required to perform the attack.
Therefore, to prevent further damage, the team at the security firm recommended upgrading all UTXO-based nodes (eg Dogecoin) to the latest version (1.14.6).
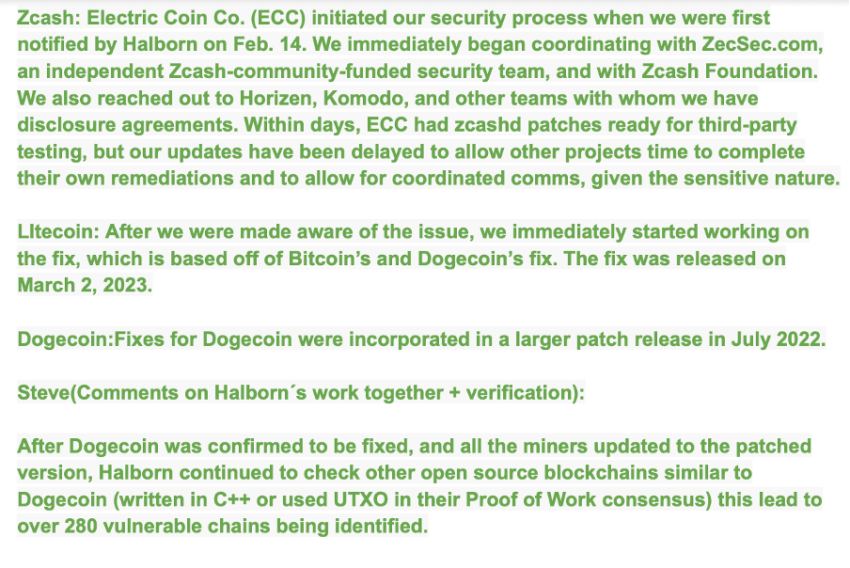
In a further conversation over the mail, the security firm answered some questions posed by BeInCrypto. When asked how Zcash, Litecoin and Dogecoin fixed the vulnerabilities, the team replied:
Such events can have implications for the wider crypto ecosystem. Steve Walbroehl, chief security officer and co-founder of Halborn, claimed:
“The longer the problems exist on public mainnets, the more likely it will be found and exploited by hackers with malicious intent. Since we had already finished working on Dogecoin, we had the biggest stakeholder already to identify a fix and solution that could be provided as example for all the other chains. It was an honorable call to action for a positive outcome with different projects working to help each other solve a common threat.”
BeInCrypto reached out to core developers at Dogecoin and Zcash for comment on this topic. However, have not yet received a response.
Disclaimer
All information on our website is published in good faith and for general information purposes only. Any action the reader takes on the information contained on our website is strictly at their own risk.
























