North Korean hackers pose as top developers to steal crypto

North Korean hackers pose as excellent candidates in recruitment campaigns. This is so that they are employed by Web3 companies. Once inside, they can steal all the digital assets of the companies that employ them. Neil Dundon of Cryptorecruit explains how it works.
Our experience with recruiting in the cryptosphere has taken a rather strange turn when it comes to North Korean hackers. We are at the coal end of this matter. It’s strange to struggle with it every day.
North Korean hackers
This behavior was first noticed by Cryptorecruit in early 2020. Although it may have been going on longer. This was a time when the crypto markets were charging up in full bull mode. Recruitment in the space exploded at unprecedented levels.
Alas! When we hired a new consultant to work with us, that consultant would often tell us about a super strong candidate they came across. I would immediately recognize it as a fake. This was always to the dismay of the new consultant!
It takes some time to work out the back story of these profiles. But then it clicks. On every single fake profile there are always telltale signs that things are not as legitimate as they seem.
We’re not making wild uneducated guesses here. We have tested such profiles thoroughly. The language they use is exactly the same in all cases – as if they are reading from a script. We can only assume they operate from a call center somewhere. Most likely it is based in the depths of North Korea.
Tell Speech Signs
The first red flag is the profile picture. It’s the ultimate giveaway. Recruiters just take a look at the shot. The sparkly applicant often claims to be Japanese. But you quickly realize that they are not Japanese at all. And then there’s the blank look in their eyes. As if they are robots, or at least generated by an AI tool. They surely have no soul.
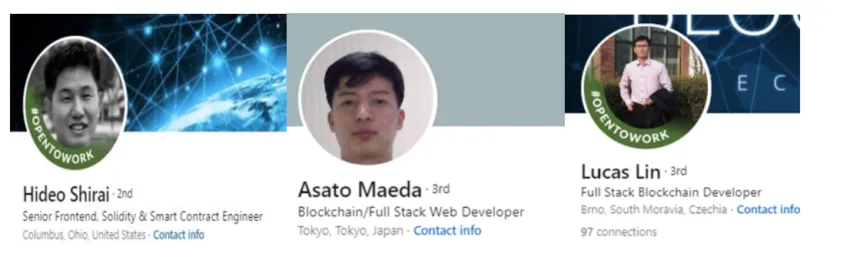
It is very unusual to see a phone number. But if there’s a phone number included, it’s a US number. They can be lured into a conversation with you. But it’s usually on Skype. And if you do connect, insist that they turn on their camera. When you see them, they don’t look like real people. They actually look like robots. It is very disturbing and strange!
North Korean hackers and the jobs they want
So what are the jobs these operators are applying for? Usually they say they are a Solidity developer, blockchain developer or something Web3 related.
Their LinkedIn profiles always use a very familiar and identifiable template. These templates are full of the most beautiful keywords. These are words that recruiters and employers in the crypto space could only hope to see on a good day.
When recruiters post a job ad, you can be sure that these fake profiles will immediately auto-respond to it. But here is the truth. Any Solidity developer worth their salt doesn’t actually apply for positions. In fact, they are targeted by recruiters all the time. They have more options on the go.
These hackers applying for jobs are probably the biggest red flag. If their profile looks fanatical and they have years of solidity experience, be careful. Of course, there can be exceptions to the rule. But be careful.

North Korean Hackers: What’s Their Motivation?
The motivation of these nefarious individuals is to get paid in crypto, and then hack defi protocols. It can take months for management to figure out that a developer is a dud. At this stage they have probably been paid $30,000 or more. And worse, had access to many of the company’s internal systems. They may have built relationships with other employees and could have had an opportunity to coerce them.
Multiply this by hundreds, or even thousands of fake profiles to get the real picture. Kim Jong Un certainly brings in pretty decent income. That will fund his nuclear program quite nicely.
My personal opinion is that employers hiring these candidates directly led to major hacks across the crypto space. In fact, the $600m Axie infinity hack was attributed to North Korean hackers without dispute.
You can protect yourself. Watch out for red flags mentioned here. Be suspicious. Ultimately, a candidate must prove who they are. And what they can do.
If you are still not sure, contact me with their Linkedin profile. My team and I are all over it.
About the author

Neil Dundon is the founder of Cryptorecruit and has over 15 years of experience specializing in recruitment. Cryptorecruit has been in the crypto space since early 2016. CryptoRecruit understands what drives sentiment in the space, whether it’s the motivation of developers to change course within blockchain companies, or your average Wall Street executive looking to enter the space.
Do you have something to say about North Korean hackers or something else? Write to us or join the discussion in our Telegram channel. You can also catch us on Tik Tok, Facebook or Twitter.
Disclaimer
All information on our website is published in good faith and for general information purposes only. Any action the reader takes on the information contained on our website is strictly at their own risk.

























