Evilnum Hacking Group updates TTPs aimed at Fintech

Cybercrime, Cybercrime as-a-service, Fraud Management & Cybercrime
Group now uses MS Office Word documents to deliver payloads
Prajeet Nair (@prajeetspeaks) •
July 2, 2022

Evilnum, a hacker group primarily targeting fintech companies in the UK and Europe, has updated its tactics, techniques and procedures using MS Office Word documents, and exploited document malinjection to deliver the malicious payload to victims’ machines.
See also: Fireside Chat | Zero tolerance: Control the landscape where you meet your opponents
In previous campaigns in 2021, the main distribution vector used by this threat group was LNK files – a type of shortcut used in Windows sent into malicious archive files as e-mail attachments in spear-phishing e-mails to victims.
Zcaler’s ThreatLabz researchers say they have identified several previously undocumented domains associated with the Evilnum group for advanced persistent threat; they say this indicates that the group has been successful in flying under the radar and has been undetected for a long time.
Security researchers discovered Evilnum in 2018 when it was found to use spear-phishing e-mail and social engineering techniques to target the financial sector, especially companies engaged in trade and compliance in the UK and Europe.
In March 2022, Zcaler researchers said they observed the group targeting an intergovernmental organization dealing with international migration services, which they describe as a significant update in the choice of targets for the Evilnum APT group.
The researchers also saw that the timeline of the attack and the nature of the attack coincided with the Russia-Ukraine conflict.
Updated technology
APT actors gain initial access to devices and networks by delivering malicious documents through a spear-phishing email campaign. After successful delivery of the malicious document, the targeted victim downloads and opens the document retrieving the macro template from the second step of the domain hosted by the attackers.
The researchers say that this asks users to activate the macro content in a certain lure content.
The template in the second step, the researchers say, contains the most important malicious macro code.
“Macro-based documents used in the malinjection stage utilized the VBA code trampling technique to circumvent static analysis and also to deter reverse engineering,” say the researchers. “This technique corrupts the original source code and only a compiled version of the VBA macro code (also known as p-code) is stored in the document.”
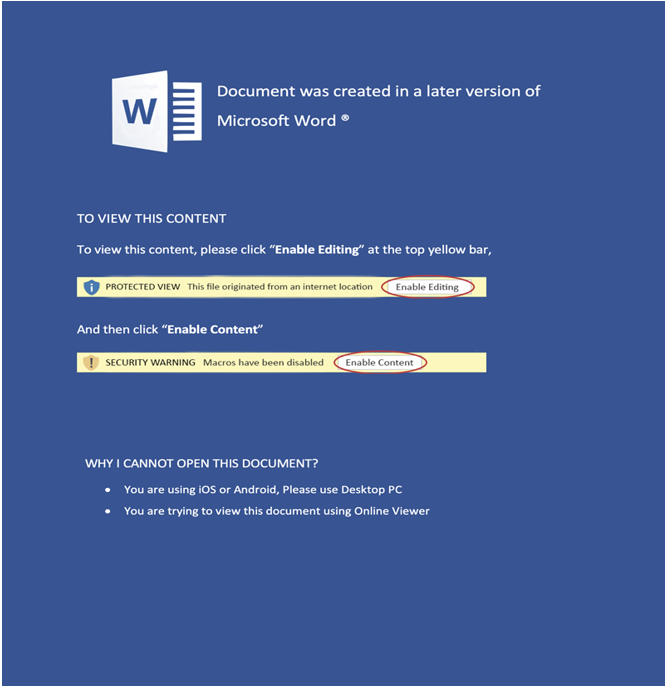
In the next step, heavily obfuscated JavaScript is used to decrypt and drop the payloads at the endpoint.
“The JavaScript configured a scheduled task to run the dropped binary. This JavaScript code has significant improvements in the obfuscation technique compared to the earlier versions used by the EvilNum APT group. The names of all file system artifacts created during the run were selected “deliberately by the threat actor to falsify legitimate Windows and other legitimate third-party binary names,” the researchers said.
The researchers also discovered that the APT group registered multiple domain names using specific keywords related to the industry’s vertical goals in each new instance of the campaign.
They observed that the threat actors achieved endurance via scheduled tasks, adding: “During JavaScript execution, a scheduled task named ‘UpdateModel Task’ ‘will be created to execute the dropped loader binary with the necessary command line arguments.”
Rear door functions
Rear doors installed in victims’ infected devices are capable of performing tasks such as decrypting backdoor configurations, resolving API addresses from libraries retrieved from the configuration, and performing mutex checks.
They are also able to create a data filtering string to send as part of the beacon request, code and encrypt the string with Base64 and enter this string in the cookie header field.
When these tasks are completed, the backdoor selects a C2 domain and a route string and sends out a beacon request. C2 can even respond with a new encrypted payload, the researchers say.
The backdoors can take screenshots and send them to the C2 server via POST requests, resulting in an encrypted format for data filtering.
The researchers say they are not sure of the origin of Evilnum, but they say that the choice of victims points to a state-sponsored interest in cyber espionage campaigns.
Previous promotions
In a previous campaign, Evilnum was seen expanding its campaigns to other countries, including Canada and Australia, the security company ESET had reported (see: APT Group targets Fintech companies).
In one of its 2020 campaigns, Evilnum distributed a remote access trojan that Cybereason researchers called PyVil. It is written in the programming language Python and includes key logging, taking screenshots of infected devices and filtering data. The Trojan can also deploy other malicious tools, such as LaZagne malware, to steal credentials, Cybereason said (see: Evilnum hackers change tactics to target Fintech companies).
A Kaspersky report in August 2020 found links between malicious software used by Evilnum hackers and variants targeted at other organizations (see: Hacking-for-Hire Group expands cyber espionage campaign).
These connections led Kaspersky researchers to conclude that Evilnum may belong to another hacker group called “DeathStalker”, which is known to target smaller law firms and financial institutions.























